This document describes how you can configure SAML Single Sign-On Authentication in Team Password Manager using Microsoft Azure Active Directory as the Identity Provider (IdP). Read the SAML Authentication document to learn how SAML Authentication works in Team Password Manager.
Follow these steps:
1. Log into Azure Portal: https://portal.azure.com
2. Open the "burger menu" on the left and select "Active Directory", and then "Enterprise Applications":
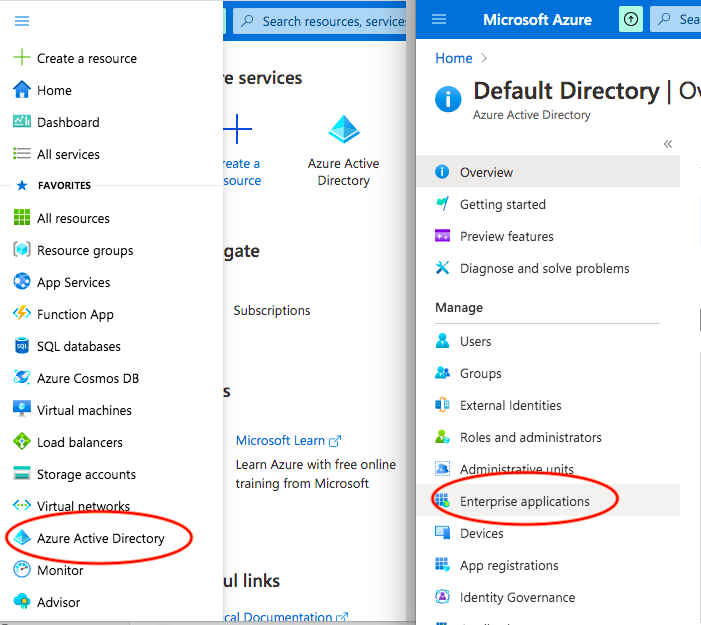
3. In "Enterprise Applications" click on "Overview", then "+ New application":
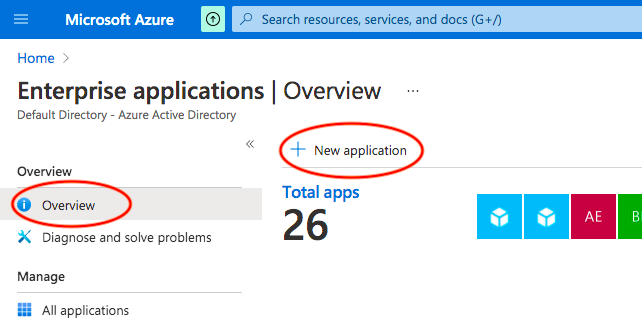
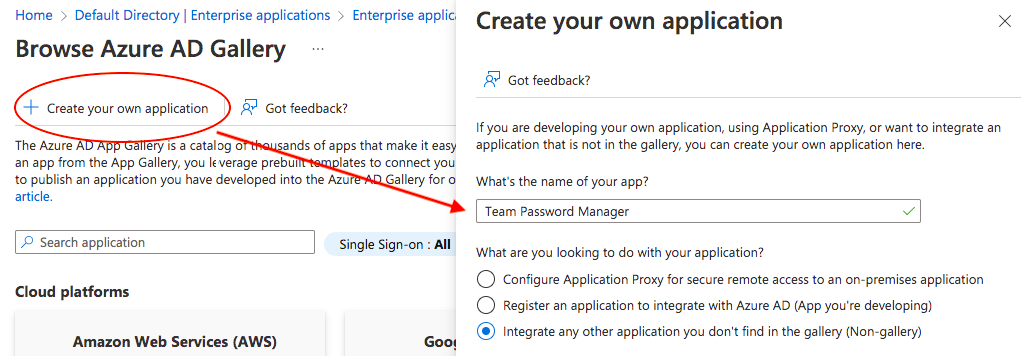
4. Select "+ Create your own application":
5. Enter the name of the application (Eg. Team Password Manager) and click on "Add":
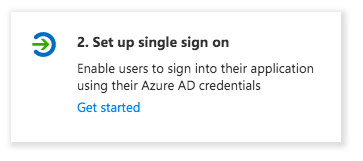
6. You'll be taken to your new application overview. Click on "2. Set up single sign on" and then select "SAML" as the single sign-on method:
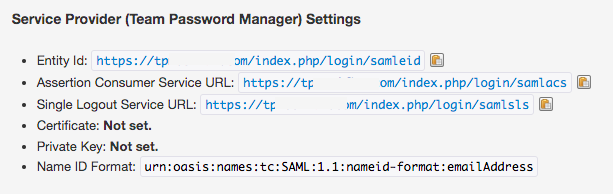
7. Copy the Service Provider (Team Password Manager) details to "Basic SAML Configuration" in Azure:
7.1 Log into your installation of Team Password Manager and go to Settings (top menu), then "SAML Authentication".
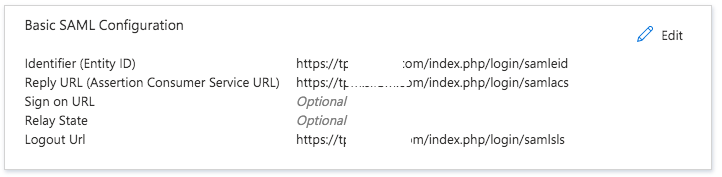
Click on "Edit" in the "Basic SAML Configuration" in Azure.
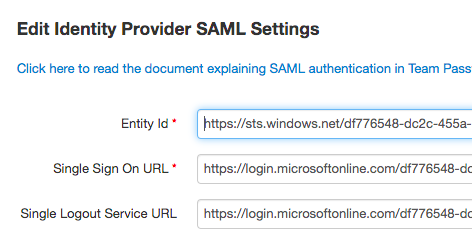
7.2 Copy the "Entity Id" value in the "Service Provider Settings" in Team Password Manager to the "Identifier (Entity ID)" field in Azure, and mark "Default".
7.3 Copy the "Assertion Consumer Service URL" value in the "Service Provider Settings" in Team Password Manager to the "Reply URL (Assertion Consumer Service URL)" field in Azure<./p>
7.4 Copy the "Single Logout Service URL" value in the "Service Provider Settings" in Team Password Manager to the "Logout Url" field in Azure.
7.5 Save in Azure.
8. In Azure, click on "Edit" in the "User Attributes & Claims" section. You'll see this:
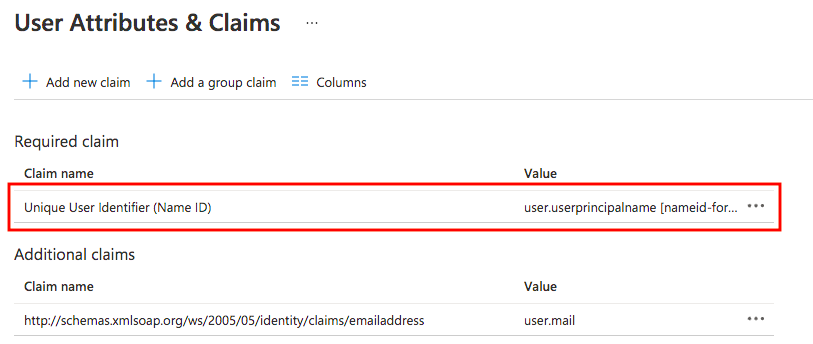
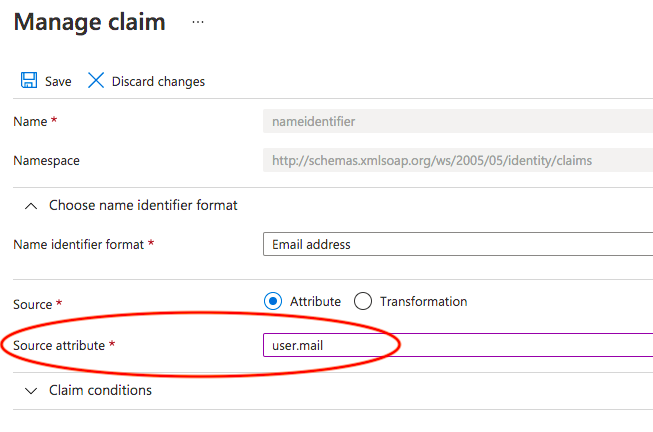
Click on the "Unique User Identifier (Name ID)", the "Manage Claim" screen will open.
In the Source Attribute (last field), select "user.mail", then "Save":
9. Copy the Azure AD SAML certificate to the "Identity Provider Settings" in Team Password Manager:
9.1 In Team Password Manager, click on "Edit Identity Provider SAML Settings".
9.2 In Azure click on "Copy to Clipboard" the "App Federation Metadata Url".
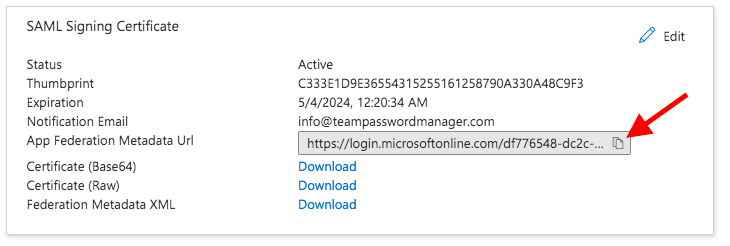
9.3 Open a new browser tab (or window) and paste the recently copied Url, you'll see something like this:
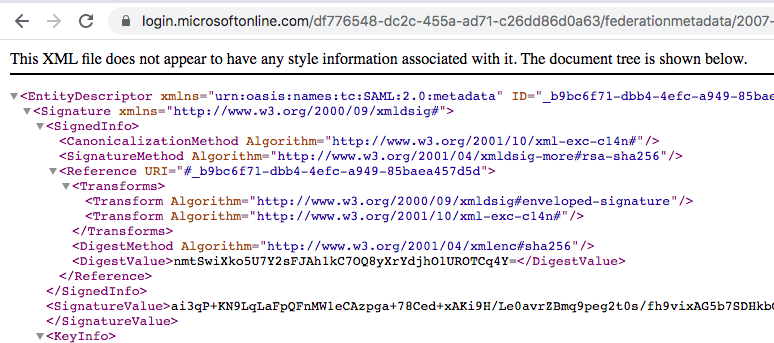
9.4 Scroll down all the contents of the page until the end and you'll see the a "X509Certificate" entry:
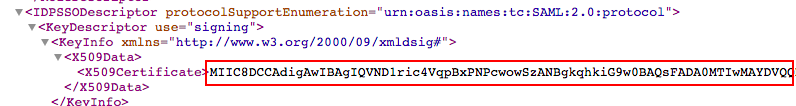
9.5 Copy to clipboard the contents of the "X509Certificate" entry (it's a long string) and paste it into the "Certificate" field in the "Edit Identity Provider SAML Settings" in Team Password Manager:
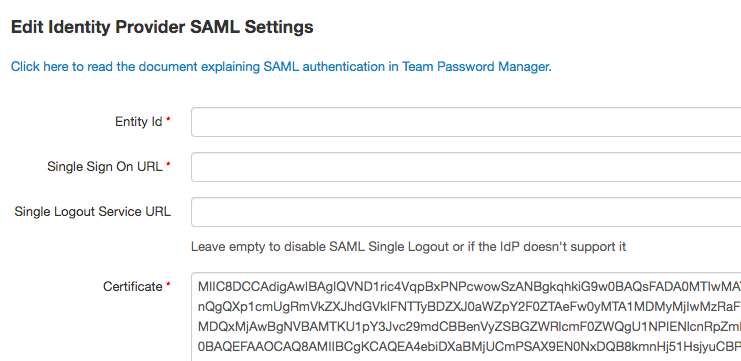
Do not close the "Edit Identity Provider SAML Settings" screen, we'll need it in the next steps.
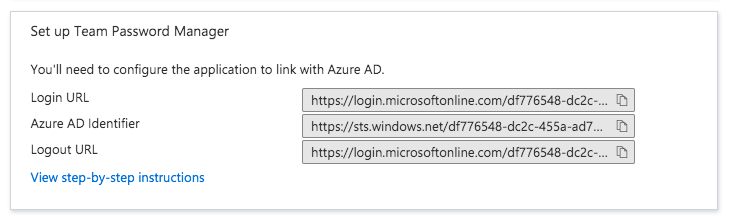
10. Copy the Identity Provider details in your installation of Team Password Manager:
10.1 Copy the "Login URL" value in Azure AD and paste it in the "Single Sign On URL" field in Team Password Manager.
10.2 Copy the "Azure AD Identifier" value in Azure AD and paste it in the "Entity Id" field in Team Password Manager.
10.3 Copy the "Logout URL" value in Azure AD and paste it in the "Single Logout Service URL" field in Team Password Manager. Note: using this field will make the user log out of all the service providers authenticated using Azure AD when the user logs out of Team Password Manager. If you don't want this to happen (so, only log out of Team Password Manager), leave this field empty.
11. Assign users and groups to the application. From the application overview screen, click on "Assign users and groups" and grant access to the application to those users/groups that need to access Team Password Manager.
SAML authentication for Azure Active Directory is now configured. To test, do this:
- Make sure you have an Admin/IT normal user in Team Password Manager. If anything goes wrong you'll be able to log in normally.
- Create a SAML user in Team Password Manager, using an email address that matches an email address of a user that has access to the Azure application just created.
- Log out of Team Password Manager and Azure.
- Click on "Sign In via SAML" in Team Password Manager. You'll be taken to Microsoft login screen and you'll need to authenticate using the email address of the user just created in Team Password Manager.
- If all goes well, you'll automatically log into Team Password Manager.
Troubleshooting
A common issue you may get with Azure is this one:
"AADSTS75011: Authentication method 'X509, MultiFactor' by which the user authenticated with the service doesn't match requested authentication method 'Password, ProtectedTransport'. Contact the Team Password Manager application owner."
If you get this message, enter the following in the SAML Custom Settings:
security.requestedAuthnContext=false
Go to Settings | SAML Authentication, click on the "Edit other SAML Settings" button and enter this line in the Custom Settings textbox.
Document changelog
| Aug 24, 2022: | Adapt steps 4, 5 and 6 to the changed interface |
| May 27, 2021: | Troubleshooting section |
| May 5, 2021: | Document created |
