This tutorial explains how to install Team Password Manager on a Linux Ubuntu 24.04 (LTS) system with the following components: NGINX, MySQL 8, PHP 8.4, Sourceguardian Loader and a commercial TLS/SSL certificate for https.
Similar versions of this tutorial with lower versions of the components can be found here: Install on Ubuntu 20.04 with NGINX and Install on Ubuntu 22.04 with NGINX.
A similar version of this tutorial with Apache instead of NGINX can be found here: Install on Ubuntu with Apache.
To be able to follow this tutorial you'll need: a running Ubuntu 24.04 LTS system (preferably with nothing else installed), which can be accessed from anywhere on the Internet, root access to this system and a non-root user which we'll use to do everything with sudo for security. You'll also need some basic Linux knowledge.
- Basic settings
- NGINX installation
- MySQL installation
- PHP installation
- Configuring NGINX to serve Team Password Manager and use PHP
- HTTPS and installing a commercial SSL Certificate
- SourceGuardian Loader installation
- Team Password Manager database and user
- Team Password Manager files
- Team Password Manager configuration file
- Team Password Manager installation script
Basic settings
We'll be creating a Team Password Manager installation that will be accessed using this URL: https://tpm.mycompany.com. We'll be referring to this URL throughout this document, so adjust it to your own URL each time.
In this section we're going to prepare the system with some basic settings:
• Make sure the system is updated with the following commands:
$ sudo apt update && sudo apt upgrade
• Update the hosts file (/etc/hosts) with the hostname and the Team Password Manager URL. To do it:
1. Get the hostname of your computer with this command: $ hostname
2. Edit /etc/hosts and enter the following line:
IP ADDRESS hostname tpm.mycompany.com
If, for instance, the IP address ofyour server is 1.2.3.4 and your hostname is tpm-hostname, this line should be:
1.2.3.4 tpm-hostname tpm.mycompany.com
• Set the timezone of your server. Here we set it to UTC with the following command:
$ sudo timedatectl set-timezone UTC
See all the timezones you can use with: timedatectl list-timezones
Check with date:
Sun Mar 9 05:49:46 UTC 2025
• Enable the firewall (ufw), also enabling SSH through it. Execute these two commands to do it:
$ sudo ufw allow ssh
$ sudo ufw enable
• Turn on network time protocol (ntp) so that the server time is synced over the Internet. This is a must if you plan to use 2 factor authentication in Team Password Manager. Execute the following commands to enable ntp:
$ sudo timedatectl set-ntp on
$ sudo ufw allow ntp
NGINX installation
We'll be using NGINX as our web server. To install it use the following command:
$ sudo add-apt-repository ppa:ondrej/nginx
$ sudo apt update
$ sudo apt install nginx
Once it's installed enable http and https ports (80, 443) through the firewall:
$ sudo ufw allow 'Nginx HTTP'
$ sudo ufw allow 'Nginx HTTPS'
Check that NGINX is running with this command:
$ sudo systemctl status nginx
To test that NGINX is running in your server you can open a web browser and type the IP address of your server in the address bar. If everything is ok you should see the following NGINX default page:
MySQL 8 installation
We're going to use MySQL 8 as the database for Team Password Manager. MySQL 8 is the default version of MySQL that installs with Ubuntu 24.04, so to install just use this command:
$ sudo apt install mysql-server
Once it's installed, run the security script to set the root password and some additional settings:
$ sudo mysql_secure_installation
You can safely set the following options in the script:
- Medium level of the password validation policy (Length >= 8, numeric, mixed case, and special characters).
- Remove anonymous users.
- Disallow root login remotely.
- Remove test database and access to it.
Once the script is finished you can test the connection using the following command:
$ sudo mysql
This will connect to the MySQL console using root because you're using sudo.
You'll be placed at the MySQL prompt: mysql>. Just type exit to return to the system prompt.
PHP 8.4 installation
Since PHP 8.4 is not the default version of PHP in Ubuntu 24.04, we'll need to add the Ondřej Surý PPA into our system. To do it, execute these two commands:
$ sudo add-apt-repository ppa:ondrej/php
$ sudo apt update
Because we're using NGINX we need to install the php-fpm (php8.4-fpm) module, which connects PHP to the NGINX. To install PHP and the modules that are required to run Team Password Manager, enter this command:
$ sudo apt install php8.4 php8.4-fpm php8.4-common php8.4-cli php8.4-mysql php8.4-mbstring php8.4-ldap php8.4-curl php8.4-gd php8.4-xml
Check that you've installed the correct PHP version using this command: $ php -v. You should see an output similar to this one:
PHP 8.4.4 (cli) (built: Feb 15 2025 08:59:26) (NTS)
Copyright (c) The PHP Group
Zend Engine v4.4.4, Copyright (c) Zend Technologies
with Zend OPcache v8.4.4, Copyright (c), by Zend Technologies
Set PHP's timezone to match the one of your server's: edit /etc/php/8.4/fpm/php.ini and set the following entry with the same timezone you set in the Basic settings section (all the PHP timezones can be found here: https://www.php.net/manual/en/timezones.php). In our case we set it to "UTC":
date.timezone = "UTC"
Configuring NGINX to serve Team Password Manager and use PHP
As stated earlier, we're going to access the Team Password Manager installation using this URL: https://tpm.mycompany.com. To make this possible, you need to do two things:
1. Create a new A/AAAA record in your DNS manager so that tpm.mycompany.com resolves to the server's IP address.
2. Configure a server block in NGINX to accept tpm.mycompany.com (for port 80 (http) and 443 (https)) and make it execute the Team Password Manager installation. (Note: server blocks in NGINX are similar to virtual hosts in Apache)
Let's explain them in more detail:
1. Go to the DNS manager for your domain and create an A record (AAAA if IPv6) for your tpm.mycompany.com subdomain, specifying the IP address of your server and the default TTL value if you need to set one. To test open the browser and enter tpm.mycompany.com in the address bar. You should see the NGINX default page. Note that this can take a while to propagate through all the DNS servers so it's normal if you don't see this immediately. Just wait for a few minutes.
2. Server blocks: server blocks allow your NGINX server to serve more than one site and configure each site with their own set of options. In this case, "site" is the Team Password Manager installation, so we'll configure one server block to serve tpm.mycompany.com. An important option we'll set up is how PHP communicates with NGINX using FPM. First we'll do the configuration for http://tpm.mycompany.com and later we'll configure https://tpm.mycompany.com with a commercial SSL certificate. Please follow these steps (remember always to change tpm.mycompany.com to your own subdomain):
2.1 Create a new configuration file for the Team Password Manager site in NGINX's sites-available folder:
$ sudo touch /etc/nginx/sites-available/tpm.mycompany.com
2.2 Edit this tpm.mycompany.com configuration file to look like this:
server {
listen 80;
server_name tpm.mycompany.com;
root /var/www/html/tpm.mycompany.com/public_html;
access_log /var/www/html/tpm.mycompany.com/logs/access.log;
error_log /var/www/html/tpm.mycompany.com/logs/error.log error;
index index.html index.htm index.php;
location / {
try_files $uri $uri/ /index.php;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/var/run/php/php8.4-fpm.sock;
}
location ~ /\.ht {
deny all;
}
}
Some explanations:
server_namespecifies the domain NGINX is serving in this block. Enter you subdomain here./var/www/html/tpm.mycompany.com/public_htmlis where we'll put the Team Password Manager software files. We'll do this later on this tutorial. Therootdirective is used to tell the web server that when a request is made to tpm.mycompany.com it should serve the files on /var/www/html/tpm.mycompany.com/public_html.- The
error_logandaccess_logdirectives create specific logs for our installation, which are stored in/var/www/html/tpm.mycompany.com/logs/. Note that these logs are web server logs, not the internal log of Team Password Manager (which can be found in the top menu of the software, "Log" option). location ~ \.php$: this location block connects NGINX with PHP using FPM.
2.3 Create the installation folders:
Execute this command to create the folders for Team Password Manager and logs:
$ sudo mkdir -p /var/www/html/tpm.mycompany.com/{public_html,logs}
public_html is the folder where we'll place the Team Password Manager files. logs is where the NGINX logs will be written for our installation.
Both folders are currently owned by root, but it's better if you assign ownership to the NGINX user and group, which for Ubuntu is www-data:
$ sudo chown -R www-data:www-data /var/www/html/tpm.mycompany.com
Then set appropriate permissions for public_html (read, write, execute for the NGINX user and group, none for others):
$ sudo chmod -R 770 /var/www/html/tpm.mycompany.com/public_html
And the permissions for log (read, write, execute for the NGINX user, read and execute for the Apache group, none others):
$ sudo chmod -R 750 /var/www/html/tpm.mycompany.com/logs
If you want your user to be able to create/edit files in public_html, you can add your user to www-data:
$ sudo usermod -aG www-data $USER
(you'll need to log out and log back in for this new group membership to apply)
Finally, ensure that new files and directories created within public_html and logs inherit the correct ownership and permissions by setting the setgid bit:
$ sudo chmod -R g+s /var/www/html/tpm.mycompany.com/public_html
$ sudo chmod -R g+s /var/www/html/tpm.mycompany.com/logs
The final result should be similar to this:
myuser@myhostname:/var/www/html/tpm.mycompany.com$ ls -la total 16 drwxr-xr-x 4 www-data www-data 4096 Mar 11 12:42 . drwxr-xr-x 3 root root 4096 Mar 11 12:42 .. drwxr-s--- 2 www-data www-data 4096 Mar 11 12:49 logs drwxrws--- 7 www-data www-data 4096 Mar 11 19:29 public_html
2.4 Activate the site by linking to the configuration file for our site from NGINX's sites-enabled folder:
$ sudo ln -s /etc/nginx/sites-available/tpm.mycompany.com /etc/nginx/sites-enabled/
2.5 Disable the default configuration file to minimize security risks by unlinking it from the sites-enabled folder:
$ sudo unlink /etc/nginx/sites-enabled/default
2.6 Test the configuration:
$ sudo nginx -t
If the configuration is correct, you should see a message like this one:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
2.7 Reload Nginx to apply the changes:
$ sudo systemctl reload nginx
To test, enter http://tpm.mycompany.com/ in your browser and you should see this forbidden message as we haven't yet put any files in the public_html folder:
Also, after accessing it, check the logs folder and you'll see the two log files: access.log and error.log.
To check that PHP is correctly installed and communicating with NGINX, do this:
1. Restart FPM to apply the changes we made in php.ini earlier:
$ sudo systemctl restart php8.4-fpm
2. Create a file called phpinfo.php in /var/www/html/tpm.mycompany.com/public_html with the following content:
<?php phpinfo();
3. Open this file with the browser pointing at your site: http://tpm.mycompany.com/phpinfo.php
You should see the phpinfo page with all the PHP settings. You can send this to PDF to keep it for your records. Afterwards, delete the phpinfo.php file.
HTTPS and installing an SSL Certificate from a Commercial Certificate Authority
Up to this point we've configured the server to accept requests to http://tpm.mycompany.com.
In this section we'll:
- Install a commercial SSL certificate to avoid browser warnings about unsafe connections.
- Configure the web server to accept requests to https://tpm.mycompany.com (note the "s" in https), so that the communication between the client's browser and the server is encrypted.
Let's get to it. We'll first begin by changing to root user and updating the system:
$ su - root (and enter the root password)
# apt update && apt upgrade
To get a commercial SSL certificate we'll need a private key and a Certificate Signing Request (CSR) file. You can create them using the following commands:
Create a folder where to store the certificate files and go to that folder:
# mkdir /root/certs/ && cd /root/certs/
Execute openssl to create the private key and CSR (remember to use your own subdomain instead of tpm.mycompany.com):
# openssl req -new -newkey rsa:2048 -nodes -keyout tpm.mycompany.com.key -out tpm.mycompany.com.csr
When you execute this you'll be required to enter some information that will be integrated into your certificate request. It's specially important that you correctly enter the "Common name", which is the URL you want to use to access your installation of Team Password Manager. In this case we've used tpm.mycompany.com because we'll use https://tpm.mycompany.com to access our Team Password Manager installation (marked in red):
Generating a RSA private key
.....................+++++
......+++++
writing new private key to 'tpm.mycompany.com.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:ES
State or Province Name (full name) [Some-State]:Barcelona
Locality Name (eg, city) []:My city
Organization Name (eg, company) [Internet Widgits Pty Ltd]:My company
Organizational Unit Name (eg, section) []:Security
Common Name (e.g. server FQDN or YOUR name) []:tpm.mycompany.com
Email Address []:info@mycompany.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
The outcome of executing openssl are two files: tpm.mycompany.com.key and tpm.mycompany.com.csr.
tpm.mycompany.com.key is the private key, and you should protect it and not disclose it to anyone. tpm.mycompany.com.csr is the CSR file. You'll be required to copy and paste its contents into the online enrollment form when requesting the certificate.
You should now purchase the certificate from a Commercial Authority (CA). We've used Namecheap (PositiveSSL certificate) but you can use any CA that you like. The CA will ask you to copy the information in the CSR file (everything from -----BEGIN CERTIFICATE REQUEST to END CERTIFICATE REQUEST-----) and paste it on the indicated form. You can see the contents of the CSR file with this command: # cat tpm.mycompany.com.csr. You'll also need to validate your domain, the CA will provide various methods for doing so.
The CA will provide you with two files: tpm_mycompany_com.crt and tpm_mycompany_com.ca-bundle. Once you have them continue with the following steps:
Copy the files to the appropriate folders:
# cp tpm_mycompany_com.crt /etc/ssl/certs/ # cp tpm_mycompany_com.ca-bundle /etc/ssl/certs/ # cp tpm.mycompany.com.key /etc/ssl/private/ # cp tpm.mycompany.com.csr /etc/ssl/private/
Delete them from the /root/cert folder:
# rm /root/cert/tpm*
Note: we advise you to store all the certificate files outside the server, in a backup location.
The certificate files should be owned by root and protected by a permission setting of 600:
# chown root: /etc/ssl/private/tpm* # chown root: /etc/ssl/certs/tpm* # chmod 0600 /etc/ssl/private/tpm* # chmod 0600 /etc/ssl/certs/tpm*
So the result of installing the certificate files should be something like this:
# ls -la /etc/ssl/certs/tpm* -rw------- 1 root root 4135 Mar 10 15:24 /etc/ssl/certs/tpm_mycompany_com.ca-bundle -rw------- 1 root root 2216 Mar 10 15:24 /etc/ssl/certs/tpm_mycompany_com.crt # ls -la /etc/ssl/private/tpm* -rw------- 1 root root 1102 Mar 10 15:24 /etc/ssl/private/tpm.mycompany.com.csr -rw------- 1 root root 1704 Mar 10 15:24 /etc/ssl/private/tpm.mycompany.com.key
Let's now tackle the NGINX configuration part. To do it, edit our site configuration file (/etc/nginx/sites-available/tpm.mycompany.com) to include the following changes:
• Listen to port 443 (ssl) instead of port 80.
• ssl directives for the certificate files:
ssl_certificate /etc/ssl/certs/tpm_mycompany_com.crt; ssl_certificate_key /etc/ssl/private/tpm.mycompany.com.key;
• Redirect http to https automatically. This is done using a new server block inside the file that listens to port 80 and redirects to the https address of the site, like this:
server {
listen 80;
server_name tpm.mycompany.com;
return 301 https://tpm.mycompany.com$request_uri;
}
The resulting configuration file should look like this (the parts in red are the ones we've just changed or added):
server { listen 80; server_name tpm.mycompany.com; return 301 https://tpm.mycompany.com$request_uri; } server { listen 443 ssl; server_name tpm.mycompany.com; root /var/www/html/tpm.mycompany.com/public_html; ssl_certificate /etc/ssl/certs/tpm_mycompany_com.crt; ssl_certificate_key /etc/ssl/private/tpm.mycompany.com.key; access_log /var/www/html/tpm.mycompany.com/logs/access.log; error_log /var/www/html/tpm.mycompany.com/logs/error.log error; index index.html index.htm index.php; location / { try_files $uri $uri/ /index.php; } location ~ \.php$ { include snippets/fastcgi-php.conf; fastcgi_pass unix:/var/run/php/php8.4-fpm.sock; } location ~ /\.ht { deny all; } }
Reload NGINX for the changes to take effect:
# nginx -s reload
You should also exit to get out of root return to the normal user.
You can now test the requests: if you go to http://tpm.mycompany.com, you should be redirected to https://tpm.mycompany.com, and see the same forbidden message as before (as we still haven't installed the software files). This time, though, you can see that the browser shows you the secure connection "lock" icon and if you click on it you'll find information about the certificate:
SourceGuardian Loader installation
Team Password Manager is a PHP web application encoded and secured using an encoder (SourceGuardian) and a loader is required to execute it. You need at least version 16.0.0 of the SourceGuardian Loader.
To install the Sourceguardian Loader follow these steps:
Go to https://www.sourceguardian.com/loaders.html and download the Linux x86_64 zip package. You should get the following file: loaders.linux-x86_64.zip.
Unzip it (it will create the "loaders.linux-x86_64" folder) and copy (or upload) the ixed.8.4.lin file into the following folder on your server: /usr/lib/php/20240924.
Edit the php.ini file in /etc/php/8.4/fpm/php.ini and put this line just below [PHP]:
extension=ixed.8.4.lin
Restart FPM (Note: we're not restarting NGINX. When we make changes to PHP configuration and we're using FPM to communicate PHP with the web server, we restart FPM instead of the web server):
$ sudo systemctl restart php8.4-fpm
To test: create a file called phpinfo.php in /var/www/html/tpm.mycompany.com/public_html with this content:
<?php phpinfo();
Open this file with the browser: https://tpm.mycompany.com/phpinfo.php
Check the "Sourceguardian" section, like in this image (note that for this tutorial the Loader version should be 16+):
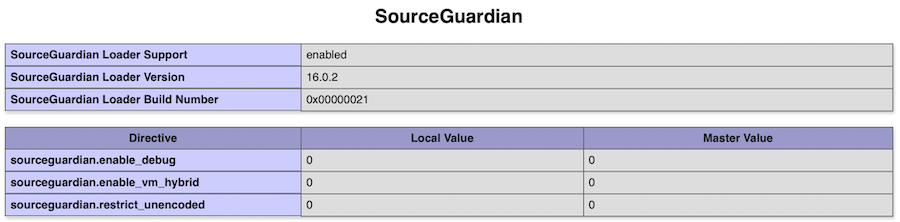
Delete the phpinfo.php file.
Team Password Manager database and user
In this section we're going to create the database that will store the Team Password Manager information and a user to access this database from the software. We're going to use these values, we advise you use your own:
Database: tpm_database
User: tpm_user
Password: tpmPass%2025
Follow these steps to create the database and user:
1. Enter the mysql prompt. Since we're using sudo, we'll log in with the mysql root user:
$ sudo mysql
2. Type the following command at the mysql prompt to create the database:
mysql> CREATE DATABASE `tpm_database` CHARACTER SET utf8 COLLATE utf8_unicode_ci;
3. Type the following command at the mysql prompt to create the user:
mysql> CREATE USER 'tpm_user'@'%' IDENTIFIED BY 'tpmPass%2025';
3. Type the following commands at the mysql prompt to grant all the privileges to the user on the database:
mysql> GRANT ALL ON tpm_database.* TO 'tpm_user'@'%';
mysql> FLUSH PRIVILEGES;
Type exit at the mysql prompt to exit mysql and return to the normal linux prompt.
Team Password Manager files
Download the Team Password Manager software files from https://teampasswordmanager.com/download/, unzip the zip file and upload all the files and folders to /var/www/html/tpm.mycompany.com/public_html.
Let's now verify permissions. We're going to assign the following permissions to Team Password Manager files and folders: full to the user and group and none to the others (770):
$ chmod -R 770 *
You should have something like this when done (myuser is the user you're using to create the installation; also note that at the time of writing this tutorial the version of Team Password Manager used is 14.168.293, so you might have different file sizes):
$ ls -la drwxrws--- 7 www-data www-data 4096 Mar 10 15:59 . drwxr-xr-x 4 www-data www-data 4096 Mar 10 12:08 .. -rwxrwx--- 1 myuser www-data 1873 Mar 10 15:59 config.php drwxrws--- 3 myuser www-data 4096 Mar 10 15:59 css -rwxrwx--- 1 myuser www-data 9262 Mar 10 15:59 eula.txt -rwxrwx--- 1 myuser www-data 610 Mar 10 15:59 folder.php drwxrws--- 2 myuser www-data 4096 Mar 10 15:59 import -rwxrwx--- 1 myuser www-data 32640 Mar 10 15:59 index.php -rwxrwx--- 1 myuser www-data 10157 Mar 10 15:59 install.txt -rwxrwx--- 1 myuser www-data 25 Mar 10 15:59 robots.txt drwxrws--- 8 myuser www-data 4096 Mar 10 15:59 system -rwxrwx--- 1 myuser www-data 4651 Mar 10 15:59 upgrade.txt drwxrws--- 2 myuser www-data 4096 Mar 10 15:59 uploads drwxrws--- 17 myuser www-data 4096 Mar 10 15:59 wmm
Team Password Manager configuration file (config.php)
Edit the config.php file and enter the database, user and password configured in the database step:
// MySQL Database server
define('CONFIG_HOSTNAME', 'localhost');
// User that accesses the database server, that should have all privileges on the database CONFIG_DATABASE
define('CONFIG_USERNAME', 'tpm_user');
// User password
define('CONFIG_PASSWORD', 'tpmPass%2025');
// Database for Team Password Manager. You must manually create it before installing Team Password Manager
define('CONFIG_DATABASE', 'tpm_database');
Team Password Manager installation script
Open your browser and enter this in the address bar:
https://tpm.mycompany.com/index.php/install
You should see the Team Password Manager installation screen:
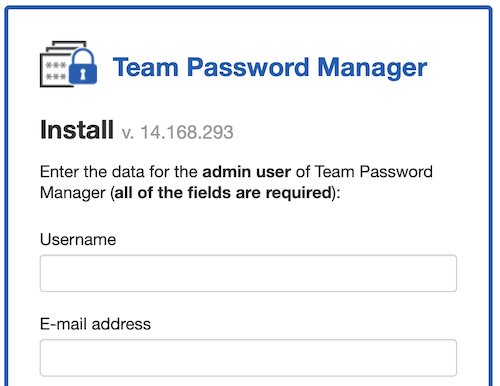
Just enter the values and complete the installation.
If everything went well Team Password Manager is now installed. Congratulations!!
Document changelog
| Mar 12, 2025: | Document created, replacing the Ubuntu 22.04 one |
