Hi everyone!
Today we're releasing a new version of Team Password Manager, 10.135.236, with many changes, two of which stand out: API v.5 and One Time Passwords.
API v.5
API v.5 introduces file management to the API. With API v.5 you can upload and download files using the API, as well as do other operations with files: list, update, etc. Basically, the same operations you can do using the web user interface. We've included examples in PHP of how you can upload and download files in the documentation.
The other main feature that API v.5 includes is full support for LDAP and SAML user management.
There are many more features in API v.5, see the full changelog here: Changes from API v4 to API v5.
One Time Passwords
Team Password Manager now can generate and store time based (TOTP) one time passwords, like Google Authenticator does. As you probably know, a one time password (OTP) is an automatically generated numeric string of characters used in two-factor authentication for login sessions.
You can easily configure a one time password by creating a custom field of type "One Time Password". When you edit the password you just have to enter the secret key provided by the web app you're setting up 2FA for and you're done. OTP values change every 30 seconds, so they're presented with a circle that closes every 30 seconds:
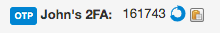
Check our One-Time Passwords document to learn more about it.
More features, including two corrected security vulnerabilities
Speaking of custom fields, we've also introduced a new type of custom field: date. A custom field of type date lets you use a calendar to enter it.
Both OTP and date custom types are fully supported by API v.5.
We've corrected two security vulnerabilities: a CSRF vulnerability when importing passwords and a way to avoid password reset poisoning.
Password reset poisoning is a technique by which an attacker manipulates the password reset link to point to a site under his control. This is done by manipulating the Host header when the reset link is generated. We've solved this by allowing you to enter the "Password reset url", which is basically the URL of your Team Password Manager installation before index.php. This way, if an attacker manipulates the Host header, the password reset link will be the same as the one we generate. You can do this in Settings | Password Reset.
Check this document on password reset to learn more about it: Password Reset for Local Users
There are many more smaller things in this release, please check the v. 10.135.236 change log to review all the changes in this version.
As always, we'd like to thank everyone who has contributed by suggesting new features or reporting bugs.
